This is the beginning of the “Hacking websites” series which will try to explain why sites are hacked, how they are hacked and how to protect your website(s) from being hacked and broken. Motivated with rather discouraging results form Breach and WhiteHat security statistics reports I decided to start these series which will, hopefully, educate readers enough to protect their websites from top 10 vulnerability classes.
Year 2009 was a “hack a web 2.0” site year. Web 2.0 sites, like Twitter, Facebook, MySpace and FriendFeed, were (and still are) according to the Breach Security The Web Hacking Incidents Database 2009 the most targeted vertical market with 19% of the total incidents with a huge jump from year 2008. The reason behind this results is in it’s popularity and the fact that all of those sites enable end user to customize and update their accounts with user-driven content, widgets and add-ons. According to Top Web Incidents and Trends of 2009 and Predictions For 2010 this enables the attackers to carefully craft and deploy Cross-Site Request Forgery (CSRF) and Cross-Site Scripting (XSS) attacks d worms toward end-users.
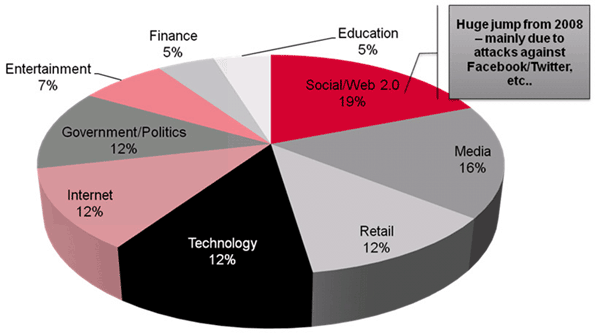
But true extent of the problems and the severity of those are visible in WhiteHat’s 8th edition of Website Security Statistic Report published in the fall of 2009. Their report is based on 1364 scanned websites with 22776 verified vulnerabilities. Key findings of the report are devastating! 83% of websites have had at least one serious vulnerability and 64% of websites currently have at least one serious vulnerability with Social Networking and Education vertical websites most likely to have serious severity issues. Even worse, WhiteHat’s finding show that vulnerability time-to-fix metrics are beginning to fluctuate, both lengthening or shortening depending on class, yet still require weeks to months to resolve.
Top ten vulnerabilities are showing that XSS is number one vector of attack. SQL inject is under-represented in the chart because industry best-practices suggest verbose error messages should be disabled to increase the difficulty of its exploitation. CSRF is also under-represented because of it’s recent appearance as a method of attack and because scanning technology industrywide is still extremely limited in its detection capability.
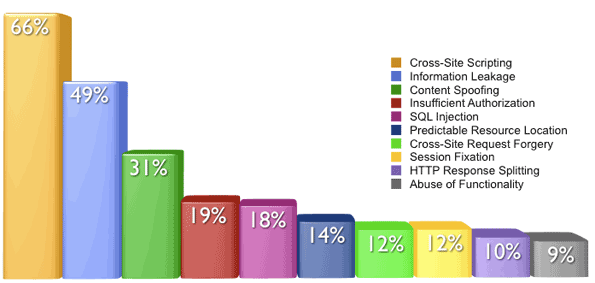
This series of blog posts will follow WhiteHat’s Top 10 Vulnerability Classes in which I will try to show how a specific vulnerability is abused, when it’s abused, what is and how to protect your website from it. In the end of the series I will compile a list of useful books which can help you understand these vulnerabilities even better. Also, there are numerous software tools on the market both free and commercial and I will try to cover most of them which might help you in finding vulnerabilities in your own websites.
DISCLAIMER: I cannot be held legally, or in any other way, responsible for any damage and/or losses of hardware, software, data or information which may be caused by using here shown instructions and/or advices. Each country has it’s own legal regulations and laws regarding here show instructions and/or advices and I recommend that you consult with your country’s responsible legal institution. Everything you do you are doing at your own risk of damage, losses and legal prosecution! All of the articles, instructions and advices shown are here for a strictly educational purposes and must not be used in any other way!
Regarding the above disclaimer, please do not try any of the shown instructions and/or advices on any of the publicly available website and/or application. If you are planning on testing your own website, please do it in a controlled environment (Testing server on your computer with a copy of your website! Do not use a public server as a testing server and do not test your or any other website while it’s live on the Internet and on a public server!) with a backup always ready in case things go wrong. During these series I will try to develop an test website which you can download free of charge on which you can learn how to protect your website.
Is there a specific attack method you would like to see explained that isn’t in the Top 10 Vulnerabilities? Is there anything else you would like to read and learn about during these series please let me know in the comments below.
Interesting post. Thanks.