In a process of hacking information system the attacker will be using one or more hacking tools to accomplish his objective. The hacking tools can be divided into two main categories: procedural classification and functional classification. Procedural classification describes which tools are use during seven steps of hacking attacker is going through. Functional classification is describing hacking tools in four main categories based on the tools functionalities and abilities.
Procedural classification
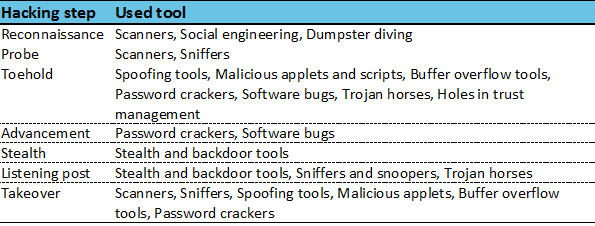
Hacking tools can be used in one or more steps of hacking and each step requires different tools. For example, in reconnaissance step while the attacker is acquiring much needed information about information system, he will be using social engineering, dumpster diving and scanners to acquire information about computers, user accounts, services and so on. Then in te second step the attacker will be using scanners and sniffers to capture important information which can be later analysed for possible vulnerabilities. Once the vulnerabilities have been found the attacker is going to use spoofing tools, buffer overflow tools, password tools and so on to obtain an entery to the information system. To obtain a privileged user account in the advancement step the attacker is going to use password crackers to obtain passwords or is going to abuse software bugs which will enable him privileged access. Once the information system is under control the attacker is going to hide his steps with stealth and backdoor tools and is going go establish listening post which will be used to gather information. That information will be used to perform a complete takeover of an information system.
Functional classification
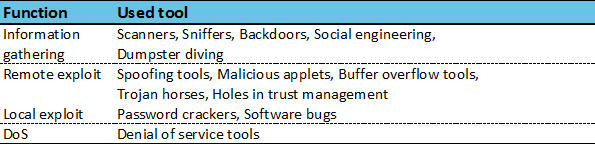
Although there are 14 kinds of hacking tool which the attacker is going to use to obtain an entry to the information system, these 14 tools can be summarized into 4 main functional categories: information gathering, remote exploit, local exploit and denial of service tools.
To gather information before and after the attack on the information system information gathering tools are used. Prior to the attack these tools will give the attacker information about vulnerabilities while after the attack these tools will be used to maintain the control of the information system. If the attacker doesn’t have access to the remote information system, remote exploit tools tools are used by the attacker to penetrate into the system. Remote exploit tools provides the attacker with the possibility of penetrating into the system without much knowledge about the system. When the attacker has gained access to the information system, local exploit tools are used by the attacker to gain access to the privileged account of the system. Denial of service tools (DoS) are used to disrupt one ore more services which can enable the attacker to do all sorts of activities. For example, DoS could be performed against some sort of logging service which enables attacker to hide his activities, or the DoS attack could be directed to some kind of internal firewall and so on.
|
Hacking step |
Used tool |
|
Reconnaissance |
Scanners, Social engineering, Dumpster diving |
|
Probe |
Scanners, Sniffers |
|
Toehold |
Spoofing tools, Malicious applets and scripts, Buffer overflow tools, Password crackers, Software bugs, Trojan horses, Holes in trust management |
|
Advancement |
Password crackers, Software bugs |
|
Stealth |
Stealth and backdoor tools |
|
Listening post |
Stealth and backdoor tools, Sniffers and snoopers, Trojan horses |
|
Takeover |
Scanners, Sniffers, Spoofing tools, Malicious applets, Buffer overflow tools, Password crackers |